With the RSA Security Conference in full swing, we sat down with Vormetric’s Vice President of Marketing, Tina Stewart, and their Director of Product Marketing, Andy Kicklighter.
Vormetric recently released their 2016 Data Threat Report. Now in its fourth year, this report not surprisingly digs deep into IoT and what it means for clouds, big data, and personal information.
Tell us a bit about this new report on Vormetric?
Tina: So from a holistic perspective, over 1,100 folks (responded) and in terms of what we are seeing, the amount of data is increasing. If you look at some of the facts we highlighted here, sensitive data is being moved in the cloud, and is coming from products that exist in your home, like Nest, and they kind of know you are gone.
Andy: IOT – and its data – is often put into a big data environment for analysis and those big data environments are often booted up in the cloud because you need the resources, so it’s almost triple jeopardy. Any threats to your data from Iot – by the time it reaches that back end – is not just Iot, it’s now data, and big data and the cloud underneath it.
So there is a lot overlap between cloud, big data, and IoT. How did you manage that?
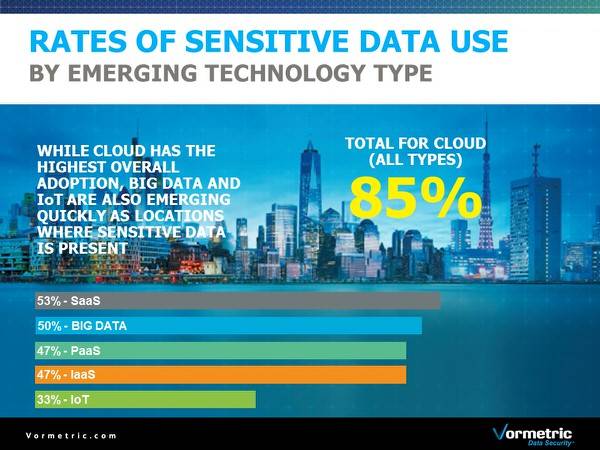
Andy: What we did was take each separately as a data case and then look for the overlaps. So from the Iot perspective, we looked at what people thought was sensitive data on their devices and we actually think those numbers are low; 31 percent in Iot, and 85 percent in the cloud. But there is so much IoT data there. I have Samsung on my wrist and that is probably pumping data back to Google or Samsung, and (while) that is probably not a lot of data, combine it with other data and it starts to become a lot more challenging, because now it’s all personal data.
In this fourth year, what trends or shifts you have seen for IoT?
Tina: I think one of the big shifts is that people are realizing that data breaches are top of mind – and it used to be compliance – so people are definitely concerned about the sensitive data with regards to what they are moving. I think from an IoT-specific point of view, it’s still in ascent and people see it as dumb information as opposed to when it goes into big data and analytics. I mean, think about Nest. People know whether you are home or gone based on how that dial is moving, and while people don’t mean to do this, but if someone who really cared about persons that way, they could rob their house. But you also could take down an entire neighborhood based on that information so they need to be able to look at how you can protect that information coming from these devices. I don’t think that the connection between IoT and the cloud in terms of data breaches is being thought about yet.
Andy: One thing to think about with IoT is that people are just getting into wide deployments now, and when you are going to market with an early product, your target is squarely to take that product to market and that is your focus. Often you are not thinking about the security ramifications until you get well past the initial deployment stage. I recently ran into someone at a show who created a lot of the smart devices for power companies for instance. And he said, well, it would be pretty easy to break into these devices. We do have secure communications between them but we don’t update them very often or patch them that often, so there is not that secure of an environment So they are having to add on security as an afterthought.
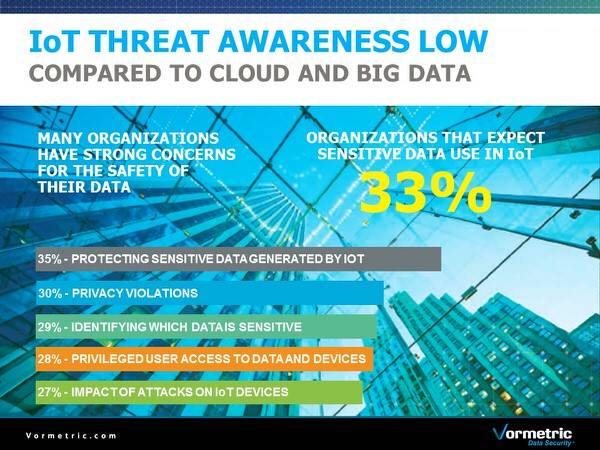
Tina: Right now, according to the survey only a third of the folks are even protecting their sensitive data. That’s such a gap when you think about it. That’s wide open. People are not seeing that data so there is a disconnect there; I found that to be surprising. When you look at data environments that are more traditional, you see that number is much higher, in the 60-70 percent (range). And part of that is what people perceive as sensitive data in IoT.
So what is “sensitive data” sounds like a moving line?
Andy: And so it’s no surprise that – in big data environments – people are worried about the sensitivity of their reports and that this information is in one spot.
Tina: I think they are missing that (it’s) only a percentage of the data they are protecting. I think they are still learning that there is a moving needle as to what is perceived as a sensitive, and if you look at the devices out here, is Fitbit sensitive information? Well, it is if it is taken advantage of, packaged together, and given to your healthcare provider. In the wrong hands, a lot of data is sensitive but on the surface it is not.
We saw this before with personal devices – like phones – getting onto company’s networks. What will be the moment where people really have to start taking this seriously?
Tina: I think it is readily approaching that (moment) because people are starting to learn in terms of how the data is being put together. In the United States, privacy is not a big deal. In the rest of the world, it is very important, so the second a major primary breach happens you are going to see people pay attention. And we have already seen that with Hello Kitty and LeapFrog – and that is pretty upsetting when your kid’s information shows up all over the Internet. That’s a huge awareness. And again, user log-in seems ok until it involves your kids’ addresses and birthdates. So a lot of the companies that are housing and using this data for analytics are looking at controls and putting them in place.
Andy: Another inflection point might be, say, if an insurance company says to put this app on your phone and wear this sensor and we will give you a better rate on your insurance – and they start monitoring where you have been, how many times you have been to McDonalds, your heartbeat, and other biometrics and start to change your rates. That is well within the capacity of today’s techniques. That is also going to make people pay attention.
And auto insurance are already doing this!
Tina: Again, the technology is helpful when used in the right way, but there are going to be inappropriate uses. I believe that as the privacy breaches become broader and hit home more personally…I mean, when I heard (about) LeapFrog, I immediately said was it one of the ones that my kids have. When people start getting down to the personal level, it starts getting disconcerting.
When you do these reports, is there a “smack my head” moment as you hear the responses?
Tina: I think I am more surprised with regards to people just not understanding where the sensitive information is. I mean, these are large enterprises, they have a lot of customer data, they have a lot of partner information – even their employee information – and they often don’t know where it is. And there are also ghosts in the machine with old applications that are sitting out there. APIs are a risk and people go after bad APIs. I definitely think the surprising thing is they just don’t know where the heck it is. And the ones that pretend they do know, that’s even worse. We walk out with our devices, we have access to all the different apps, and we have our personal phones that we use for work as well. It’s very natural behavior now.
Andy: As professionals are looking at implementing these environments, they are not looking at what kinds of policies they need to ensure that peoples’ data is protected. Do they have an expiration policy? Do they know how long they keep the data? Do they have a policy (stating) how they are going to protect it, and who has access to it? What happens to it over time? What happens if they are acquired? I can get that information from my bank and my credit card company, but am I going to get it from people making my thermostat and my smart refrigerator? Mostly these policies are not in place.





