
Naoki Hiroshima survived an Internet security nightmare earlier this week, though not without first acquiescing to the demands of the person who hacked him.
Someone claimed to obtain the personal information and passwords of Hiroshima’s GoDaddy and PayPal accounts, changed them, and held the accounts as hostage. All he asked for was one thing: access to Hiroshima’s Twitter account.
Hiroshima’s account is one of the very few precious accounts that are only one letter—@N. Many Twitter users want to get their hands on limited usernames, like those containing one letter or the ones belonging to the elusive first name Twitter club. But this hacker went so far as to compromise other accounts linked to Hiroshima’s business and financial information.
The hacker described his tactics in an email to Hiroshima.
– I called paypal and used some very simple engineering tactics to obtain the last four of your card (avoid this by calling paypal and asking the agent to add a note to your account to not release any details via phone)
– I called godaddy and told them I had lost the card but I remembered the last four, the agent then allowed me to try a range of numbers (00-09 in your case) I have not found a way to heighten godaddy account security, however if you’d like me to recommend a more secure registrar i recommend: NameCheap or eNom (not network solutions but enom.com)
PayPal claims Hiroshima’s account was not compromised, and the company never provided the alleged hacker with any personal details. GoDaddy, on the other hand, was duped.
GoDaddy CEO Blake Irving confirmed to ReadWrite that the company was “socially engineered,” meaning the hacker manipulated GoDaddy into divulging personal information by posing as the account owner.
I reached out to the alleged hacker, and he told me in our initial email contact he would be willing to share his story. Unfortunately, it appears he deleted his email account and broke off all contact with me. I’ll update the story with his comments if I hear back.
Twitter Handles Are Precious Real Estate
After reading about Hiroshima’s experience, a handful of other Twitter users claimed their accounts had received similar hacking attempts.
Josh Bryant, founder of file sharing service Droplr and the owner of the @jb Twitter account, also suffered an extortionist hack. In his case, the hacker compromised his Amazon Web Services account, putting his entire business in jeopardy—simply because the attacker wanted to own his Twitter handle.
One way hackers attempt to get access to Twitter accounts is through the “forgot password” link on a user’s account. People can find out if someone is attempting to access their account when they receive password reset emails.
Kevin Cheng, CEO of Incredible Labs in San Francisco and owner of the Twitter account @k, told me he used to frequently receive password reset emails, but once Twitter began requiring some personal information to ask for a reset password, those attempts mostly stopped.
The company implemented two-factor authentication last May as a way to prevent would-be hackers from attempting to access Twitter profiles. With two-factor authentication, users can choose to protect their Twitter accounts by providing a phone number that Twitter can text anytime someone attempts to login to their account from a new device.
You’ll Pay How Much For My Name?
What struck me after reading Hiroshima’s blog post about his Twitter extortion was that he had been offered as much as $50,000 for his username. And he turned it down.
Multi-thousand dollar offers for Twitter handles aren’t unusual. According to the New York Post, JPMorgan Chase, the banking and financial services company, offered Chase Giunta, owner of the @Chase Twitter handle, $20,000 for his username.
Buying and selling usernames is against the rules on Twitter, but there is little the company can do to combat it. Most deals are done quickly and quietly—money exchanges through PayPal accounts and the Twitter handle is transferred.
While frowned upon by the establishment, this practice happens more often than you might think.
Squatting and flipping valuable usernames isn’t a phenomenon exclusive to Twitter. My friend pointed out that he used to do the same for Gmail email addresses when the service first launched.
Twitter is aware its users are in the market for usernames. But beyond chastising the buyer or seller, there is little they do.
Joshua Ziering, subversive marketer and founder of Killswitch in San Francisco, has bought and sold around six Twitter usernames. He said it largely happens privately behind the scenes, sometimes initiated with a Twitter direct message.
Ziering said he spent time as a “fixer,” and was responsible for getting people and companies things like domain names, Twitter handles and other social media properties.
“It is a lot of work to track down these people, contact them, then negotiate for all the assets,” Ziering said. “Once someone knows they own the Twitter handle your company wants, they charge much more. Especially if you’ve been funded publicly.”
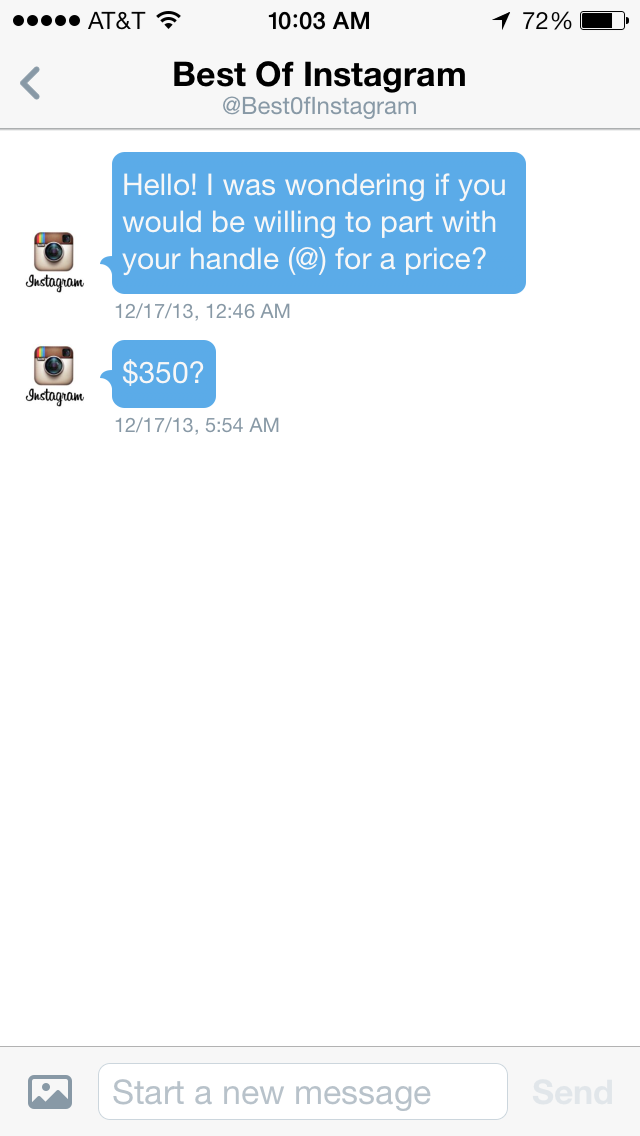
Michael O’Donnell, photographer and proud owner of the @photo Twitter handle, has been approached numerous times for his username. O’Donnell said he was contacted frequently in early 2013, but interest has since dropped off. One account offered him $350 for his Twitter handle, an offer he declined.
Righting Twitter Wrongs
For some, like the companies Ziering helped facilitate, owning the right Twitter handle is important for a brand image. But for malicious hackers, sometimes they want to acquire an account just for the fun of it.
Hiroshima’s hacker wanted nothing more than to own the username. It wasn’t for the followers—after the hacker took control of the account @N had just around 300 followers. It was simply because they could.
This puts Twitter in an interesting position. The company deals with account hijackings fairly regularly—if someone’s account is hacked, Twitter can suspend the account and work with the rightful owner to get things back to normal. Unfortunately, because Hiroshima gave the hacker access to his account willingly, albeit because of blackmail, the situation became a little more difficult for the company to control.
It appears Twitter suspended the @N account in an effort to put things back to normal, but it was compromised once again by another user before Hiroshima got it back.
Account hijackings aren’t unique to Twitter; it’s a consequence of online living. There are certain precautions to take, like implementing two-factor authentication and maintaining strong passwords, to better prevent potential security breaches.
It’s unlikely those of us with generic Twitter usernames will ever be approached to give up our handle, or be hacked specifically for it. But Hiroshima’s experience serves as an unfortunate reminder of just how insecure our online properties can be, and how simple it is for the system to be manipulated.
Lead image via eldh on Flickr.





